Defining the "Who" Conditions
In the Who? section of the Create Alert/Prevent Rule page, you can define (or edit) the individual(s) or groups of users who performed the activity on which an alert will be generated. The "Who?" condition can be configured for both alert and prevent rules.
You should use the "Who" options to define conditions based on usernames of shared accounts or domain name. These options can also be used to exclude specific users for specific rules. In order to apply the rule on specific users or on all users in an organization, it is recommended that you use the rules assignment feature. For details, see Configuring Alert Rule Assignments.
To define the "Who?" conditions
-
Open the Who section by clicking
 or the Edit
or the Edit icon.
icon.Before you begin, make sure that you have read "Rules for Configuring Alert Conditions" described in Understanding the Logic for Defining Rule Conditions.
-
To define the individual(s) or groups of users who performed the activity on which an alert will be generated, select the relevant user type options, as described in the following table.
Options for Defining the "Who" Conditions
|
Field Option |
Operators |
Usage Examples |
|---|---|---|
|
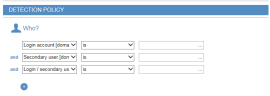
Login account [domain\]name |
is is not contains does not contain starts with does not start with ends with does not end with is member of group is not member of group |
Use this option to generate an alert based on one or more login account names (optionally including a domain) with which the user(s) logged in. Examples:
|
|
Secondary user [domain\]name |
Use this option to generate an alert based on user accounts used for secondary authentication. (Secondary authentication accounts are defined in the Active Directory or directly in ObserveIT.) Secondary authentication is typically used to differentiate between various admin users who log in using the same shared admin-level account (for example, administrator or root). For example:"Secondary user [domain\]name is observeit-sys\james" | |
|
Login/Secondary user [domain\]name |
Use this option to generate an alert based on either the login account name or secondary authentication login account name. For example: "Login/Secondary user [domain\]name contains observeit.com\john" |