mTLS Authentication Certification
Mutual TLS (mTLS) authentication strengthens the security of ITM On-Prem (ObserveIT) communications by adding certificate-based authentication of Agents to the Server. When mTLS is enabled, the Agent and the Server exchange their public key certificates to validate each other's identity. This helps prevents illegitimate Agents from compromising the system integrity.
When using mTLS, certificates for both the Server and the Clients (Agents) are required. A Client certificate needs to be distributed and installed so that client’s Agent will be able to connect to the Server once mTLS is enabled.
This topic describes the requirements for Client certificates and provides some examples about creating Client certificates using various Windows utilities. These are provided as examples only and may not be suitable for use in your environment. The certificate hierarchy, certificate lifetimes, key lengths, and other aspects of key management should be determined by your organization.
Generating an Client (Agent) Certificate using MMC (Example)
This procedure describes an example of how to request a client certificate using Microsoft Management Console (MMC).
In this procedure MMC is used. You can use any management software.
In mTLS setup, if you want to replace the Client certificate, add the new certificate and remove the older certificate. This allows the connection to resume.
-
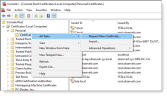
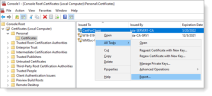
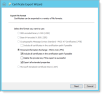
From Microsoft Management Console (MMC), navigate to Certificates > Personal > Certificate.
-
Right-click and select All Tasks > Request New Certificate.
-
Click Next to see the list of Request Certificates.
-
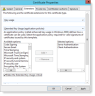
The Certificate Properties dialog box opens. Locate the certificate you want and click More information is required to enroll this certificate. Click here to configure settings to open the Certificate Properties.
-
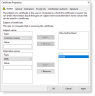
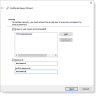
In the Subject tab:
- Subject name > Type , select Common Name and type the name in the Value field. Click Add.
- Alternative name > Type, select DNS and type itAuth in the Value field. Click Add.
-
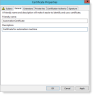
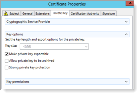
In the General tab:
- Complete the Friendly name and Description fields.
-
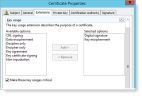
In the Extension tab:
- Select Key usage and verify Digital signature and Key enciphement are Selected options.
- Click OK.
- Select Extended Key Usage and verify Server Authentication and Client Authentication are Selected options.
- Click OK.
-
In the Private Key tab:
- From the dropdown, select Key options and select Make private key exportable.
-
Click Apply.
You are returned to the Certificate Enrollment. Select the certificate.
-
Click Enroll.
You are returned to MMC.
-
Navigate to Certificates > Personal > Certificate. Right click and select All Tasks > Export.
-
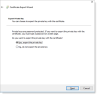
The Certificate Export Wizard opens. Click Next.
-
Select Yes, export private key. Click Next.
-
Select Export all extended properties. Click Next.
-
Select complete the password fields. Click Next.
-
Name the file. Click Next.
-
Review your settings and click Finish.
Your certificate has been exported. You can install this certificate on the endpoint (client-side).
Generating a Client (Agent) Certification using PWS (Example)
This section describes an example of how configure client certification using Microsoft Personal Web Server (PWS).
In this procedure PWS is used. You can use any Web server software.
You must include -DnsName itAuth as shown in the example.
-
Open PWS as Administrator.
-
Run the following:
New-<SelfSignedCertificate> -Type Custom -DnsName itAuth -KeySpec Signature -Subject "CN=<FQDN of the Application server>" -KeyExportPolicy Exportable -HashAlgorithm sha256 -KeyLength 2048 -CertStoreLocation "Cert:\localmachine\My" -Signer $cert -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.2")
Related Topics:
ITM On-Prem (ObserveIT) Remote Architecture
Redirecting ITM On-Prem (ObserveIT) Agents for mTLS Infrastructure