Securing Images on the File System
To secure images on the File System, a PKI-based mechanism is used to encrypt and digitally sign all session images.
The following steps are required to secure images on the Application Server:
-
Obtain a digital certificate.
-
Install the digital certificate.
-
Enable Image Security on the Application Server.
- Note: Enabling image security might slightly impact CPU load on the Application Servers.
Step 1 - Obtaining a Digital Certificate
The first step in enabling image security is to obtain a Digital Certificate for each Application Server. A Digital Certificate is the digital equivalent of an ID card used with a public key encryption system. Also called digital IDs, digital certificates are issued by trusted third parties, known as certification authorities (CAs). The process of obtaining a digital certificate is beyond the scope of this documentation. This guide assumes that the reader holds prior knowledge of PKI and its related terminology.
There are several ways you can obtain a Digital Certificate; from a self-signed source, from an internal Certificate Authority (CA), or from a 3rd-party commercial CA.
For instructions on how to obtain a self-signed digital certificate, see Creating a Self-Signed Digital Certificate.
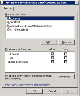
The following screen provides an example of a Digital Certificate request from a Windows Server machine to an internal Enterprise Certificate Authority.
You should provide a "friendly" name for the certificate such as "ITM On-Prem (ObserveIT) Certificate".
After the Digital Certificate is obtained, it will be used in the process of encrypting and decrypting the images.
Important: It is very important that you maintain a proper backup of this Digital Certificate and the associated Private Key. This can be done by exporting it to a .PFX file and keeping it in a safe place. The .PFX file is also used to import the Digital Certificate and the associated Private Key to additional Application Servers.
Step 2 - Installing the Digital Certificate
To install the certificate using the Internet Information Services (IIS) Manager Microsoft Management Console (MMC).
This certificate must be installed on the Web console and on all Application servers.
You can ignore the expiration date of the certificate. It does not need to be renewed.
-
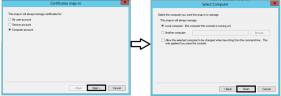
Go to Start > run and enter mmc.
-
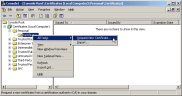
In the Console window, select File > Add/Remove Snap-in.
-
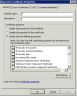
Select the Certificates snap-in, click Add, and assign it to the local computer account (Computer Account -> Local Computer).
-
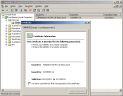
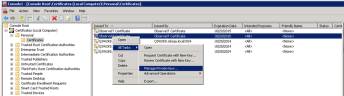
In the MMC, under Local Computers > Personal, right-click the certificate and select All Tasks > Manage Private Keys.
-
Grant the certificate full privileges for the Everyone group.
Step 3 - Enabling Image Security on the Application Server
To enable image security on the Application Server
-
Navigate to Configuration > Security & Privacy.
-
In the Security tab, if required, select the Enable Session Data Integrity check box.
By default, the Enable Session Data Integrity check box is disabled. When this check box is enabled, a security check is run on all sessions in the database. If the security check finds any sessions that may have been modified, a
 warning icon will appear next to the relevant sessions in the Server Diary or User Diary, or in the video replay of the Session Player.
warning icon will appear next to the relevant sessions in the Server Diary or User Diary, or in the video replay of the Session Player. -
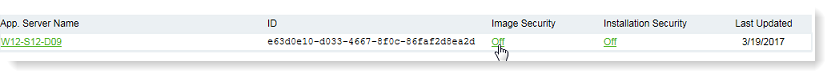
Under Image Security, click the Off link.
-
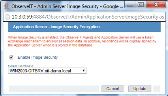
In the Application Server - Image Security Encryption window, select the Enable Image Security check box. Make sure the Digital Certificate listed matches the one you have obtained for the Application Server. If no Digital Certificate is listed, the image security cannot be enabled.
Selecting Enable Image Security updates only for the selected App server and does not apply on all application servers. To enable it for all servers, you must change the Image Security setting to ON for each application server.
-
Click the Update button.
-
Click OK to acknowledge the changes.
The images will now be protected in the database.
- Important: If you have previously set SSL for communicating with the ITM On-Prem (ObserveIT) Management console or the ITM On-Prem (ObserveIT) Application Server (see Enabling SSL/TLS on the Application Server/Web Console Server and Configuring an ITM On-Prem Windows Agent (ObserveIT Windows Agent) to Use SSL/TLS in the Installation Guide), you CANNOT use the same SSL certificate for the encryption of images. The certificate MUST be configured for at least Encrypting File System purposes.
Related Topic: